Console Initial Setup
Prerequisites
- Access to Keycloak Master Realm
- SSO has been setup for:
SSO setup for tools that are disabled is not required.
Keycloak
SmoothGlue can automatically configure this client and group out of the box. Please see the SmoothGlue auto-SSO feature. Skip to Create Console-Bot Admin User if not manually setting up the Keycloak client and group.
Create Keycloak Client
- In the
smoothgluerealm, click onClientsunderManagein the left pane. - Click
Create client. - Ensure the
Client typeisOpenId Connect. - Enter a unique client name (e.g.,
console) forClient ID. - Click on the
Nextbutton. - Ensure
Client authenticationis toggled on,Standard flowis enabled, andDirect access grantsis disabled - Click on the
Nextbutton. - Set
Valid Redirect URIstohttps://console.${DOMAIN}/login/generic_oauth. - Set
Valid post logout redirect URIstohttps://console.${DOMAIN}. - Click on the
Savebutton.
Configure Dedicated Mapper
- Go to the
consoleclient and click on theClient scopestab. - Click on the
console-dedicatedclient scope. - Click
Configure a new mapper. - Select
Group Membership. - Enter
console-group-membership-mapperforName, - Enter
groupsforToken Claim Name. - Click
Save.
Configure _structsureAdmins Group
Console assigns SmoothGlue admins configured in Console to the _structsureAdmins group in Keycloak. It is important that this group has the realm-admin role mapping so that admins can manage users in Keycloak via Console:
- In the
smoothgluerealm, clickGroupsin the left-hand panel. - Select
_structsureAdmins. - Go to
Role mappingtab. - Click
Assign role. - Ensure the drop-down filter in the top left is set to
Filter by clients. - Search for and enable the
realm-adminrole. - Click
Assign.
Configure Console for Keycloak
Console uses authservice to get a Java Web Token (JWT) from Keycloak that contains info about the currently logged-in user. Console uses the permissions of the logged-in user to interact with Keycloak APIs to manage user accounts.
If Keycloak is using non-publicly trusted or self-signed certificates, Console will need to be configured with additional CAs in order for Console to talk to Keycloak.
The following is automatically configured when using the SmoothGlue auto-SSO feature.
Add the following to bigbang-secrets.yaml:
addons:
authservice:
chains:
console:
callback_uri: https://console.<DOMAIN>/login/generic_oauth
match:
header: :authority
prefix: console.<DOMAIN>
client_id: console # the client name created above
client_secret: <client_secret> # retrieve the client secret from the client's `Credentials` tab in Keycloak
packages:
console:
values:
backend:
keycloak:
realm: smoothglue
host: keycloak.<DOMAIN> # this value can be omitted but is required when setting a custom subdomain for Keycloak.
caBundle: |
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
Create Console-Bot Admin User
We recommend starting with an initial Keycloak bot-admin user with the realm-admin role in order to be responsible for downstream tool access tokens. This bot-admin will be used to set up access keys within tools that Console supports integrations for.
Do not log in to Console UI with this user. It is recommended to remove the password for console-bot in Keycloak to reduce the chances of downgrading permissions.
- In the
smoothgluerealm, clickUsersin the left-hand panel. - Click
Add user. - Fill in the following information for the initial user:
- Email verified: Enabled
- Username:
console-bot - Email:
console-bot@<your-domain>.com - First name:
console - Last name:
bot - Groups:
_structsureAdmins
- Click
Create.
Set a password for the console-bot user:
- From the
smoothgluerealm, go toUsers>console-bot. - Go to the
Credentialstab. - Click
Set password. - Disable
Temporary. - Enter a password.
- Click
SaveandSave passwordto confirm.
Do not log in to Console UI with this user.
Configure Console Integrations
Console has integrations with the following tools for managing users and access to resources:
- GitLab
- Mattermost
- Jira
GitLab
Users are dynamically created upon logging in to GitLab, so you'll need to log in as the console-bot user in order to create the user within GitLab.
After logging in as console-bot, log out of GitLab and log in as the default admin user for GitLab.
Assign admin privileges to the console-bot user:
- Go to the admin panel by clicking
Adminnear the bottom-left of the screen or by going tohttps://{{GitLab_Hostname}}/admin. - Go to
Users. - Click
Editfor theconsole-botuser. - Change
Access leveltoAdministrator - Click
Save changes.
Create Personal Access Token:
- Log in to GitLab as
console-bot. - Click the user icon in the top-left corner, and select
Preferences. - Click
Access Tokenson the left-hand panel. - Click
Add new token:- Name:
console-bot-admin-integration. - Set an appropriate expiration date for the environment. This token will need to be manually rotated.
- Scopes:
apiandadmin_mode. - Click
Create token.
- Name:
- Save the value for the token.
Removing or altering permissions in GitLab for console-bot after access tokens have been set could lead to unexpected issues.
To configure Console to use the access token, the following configuration should be placed into the bigbang-secrets.yaml:
packages:
console:
values:
backend:
gitlab:
enabled: 'true'
accessToken: '<Personal Access Token Value>'
host: 'gitlab.<DOMAIN>' # this value can be omitted but is required when setting a custom subdomain for GitLab.
Jira
Users are dynamically created upon logging in to Jira, so you'll need to log in to Jira as the console-bot before proceeding.
Assign admin privileges to console-bot user:
- Log in to Jira with an admin-level account.
- Click on the
Settingsgear icon in the top-right corner. - Click
User management. - Edit user groups for
console-botby clicking the kebab icon (3 vertical dots) to add the following groups:jira-administrators
Create Jira Personal Access Token:
- Log in to Jira as
console-bot. - Click the user icon in the top-right corner, and go to
Profile. - Click
Personal Access Tokensin the left-hand panel. - Click
Create token:- Token name:
console-bot-admin-integration. - Disable
Automatic expiry.
- Token name:
- Click
Create. - Save token value.
Removing or altering permissions for console-bot in Jira after access tokens have been set could lead to unexpected issues.
To configure Console to use the access tokens, the following configuration should be placed into the bigbang-secrets.yaml:
packages:
console:
values:
backend:
jira:
enabled: 'true'
host: 'jira.<DOMAIN>' # this value can be omitted but is required when setting a custom subdomain for Jira.
accessToken: '<Jira Access Token Value>'
envs:
JIRA_USERNAME: 'console-bot'
Mattermost
Users are dynamically created upon logging in to Mattermost, so you'll need to log in to Mattermost as the console-bot before proceeding.
Enable Personal Access Tokens for Admins:
- Log in to Mattermost with an admin-level account.
- The user will be prompted to create a team. This can be named/configured to the user's preference.
- Click the 9 dot icon in the top-left corner (left of the Mattermost logo).
- Click
System Console. - Click
Integration Managementin the left-hand panel. - Enable Personal Access Tokens:
True. - Click
Save. - Leave
System Consoleby clickingBack to <team name>.
Enable Admin for console-bot:
- Log in using a Mattermost admin-level account.
- Click the 9 dot icon in the top-left corner (left of the Mattermost logo).
- Click
System Console. - Navigate to
User Management->Users. - Find
console-bot, and in theActionscolumn, selectManage Rolesand set toSystem Admin. - Click
Save.
Create Personal Access Token:
- Log in to Mattermost as
console-bot. - Click the profile icon in the top-right corner.
- Click
Profile. - Click
Security. - Click
EditforPersonal Access Tokens. - Click
Create Token:- Token Description:
console-bot-admin-integration. - Click
Yes, Create.
- Token Description:
- Save
Access Tokenvalue.
console:
values:
backend:
mattermost:
enabled: 'true'
host: 'chat.<DOMAIN>' # this value can be omitted but is required when setting a custom subdomain for Mattermost.
accessToken: '<Mattermost Access Token Value>'
Removing or altering permissions in Mattermost for console-bot after access tokens have been set could lead to unexpected issues.
Create Admin User
Now that the console-bot user access tokens have been set up, the next step is to create the initial admin user that will serve as the first user in Console UI.
- First, navigate to Keycloak and follow the same steps to set up an admin user in Keycloak:
This user will serve as the initial first admin and user within Console UI. The naming convention is up to the user; however, avoid the username admin, as it is reserved in some tools.
- In the
smoothgluerealm, clickUsersin the left-hand panel. - Click
Add user. - Fill in the following information for the initial user:
- Email verified: Enabled
- Username:
<your-desired-admin-username> - Email:
<your-desired-admin-username>@<your-domain>.com - First name:
<your-desired-admin-first-name> - Last name:
<your-desired-admin-last-name> - Groups:
_structsureAdmins
- Click
Create.
Set a password for the admin user:
- From the
smoothgluerealm, go toUsers>your-desired-admin-username. - Go to the
Credentialstab. - Click
Set password. - Disable
Temporary. - Enter a password.
- Click
SaveandSave passwordto confirm.
Adopt User and Promote to Admin
Now that the user account has been created in Keycloak, we can log in to Console UI and it will be adopted by the system.
-
Navigate to Console UI and log in using
your-desired-admin-usernameand password set up in Keycloak. -
Once successfully logged in, the user will exist in Console but not have admin privileges.
-
Get the
console-backendpod name from the cluster:kubectl get pod -n console | grep "console-backend". -
Get a shell on the backend pod:
kubectl exec -it <console-backend-pod-name> -n console -- sh. -
Promote the user to platform admin by using the create_platform_admin script.
- Enter
django-admin create_platform_admin. - When prompted, enter the username for
<your-desired-admin-username>that was created in Keycloak. - Console UI should update automatically, but the session might require a refresh and/or a relogin, using the same credentials.
- Enter
-
Once the user is updated, at the top right of the screen where the username is located, there should be a drop-down that will have an option to toggle between admin and user mode. Select the
Admin Panelview: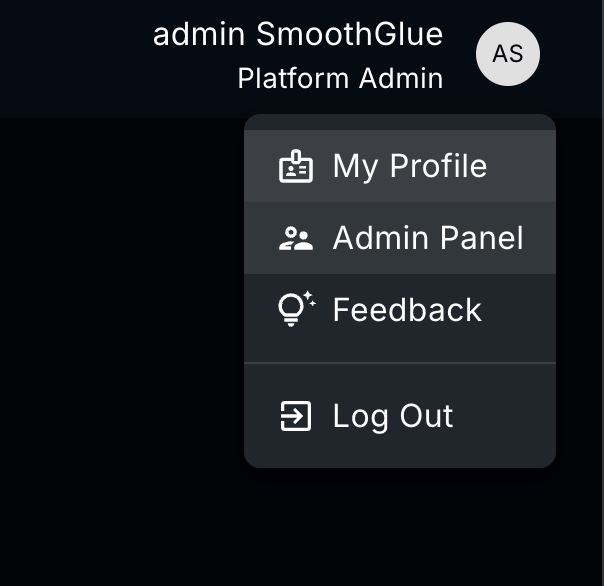
-
Navigate to the
Usersview on Console UI: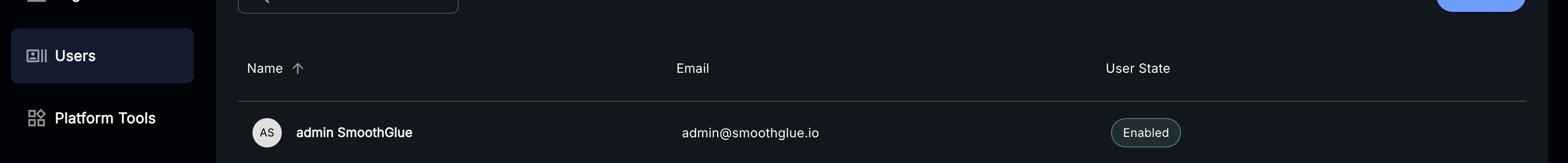
-
Repair the initial admin user created for Console use:
noteRepairing a user in Console UI will create the user in the following downstream tools:
- GitLab
- Mattermost
- Jira
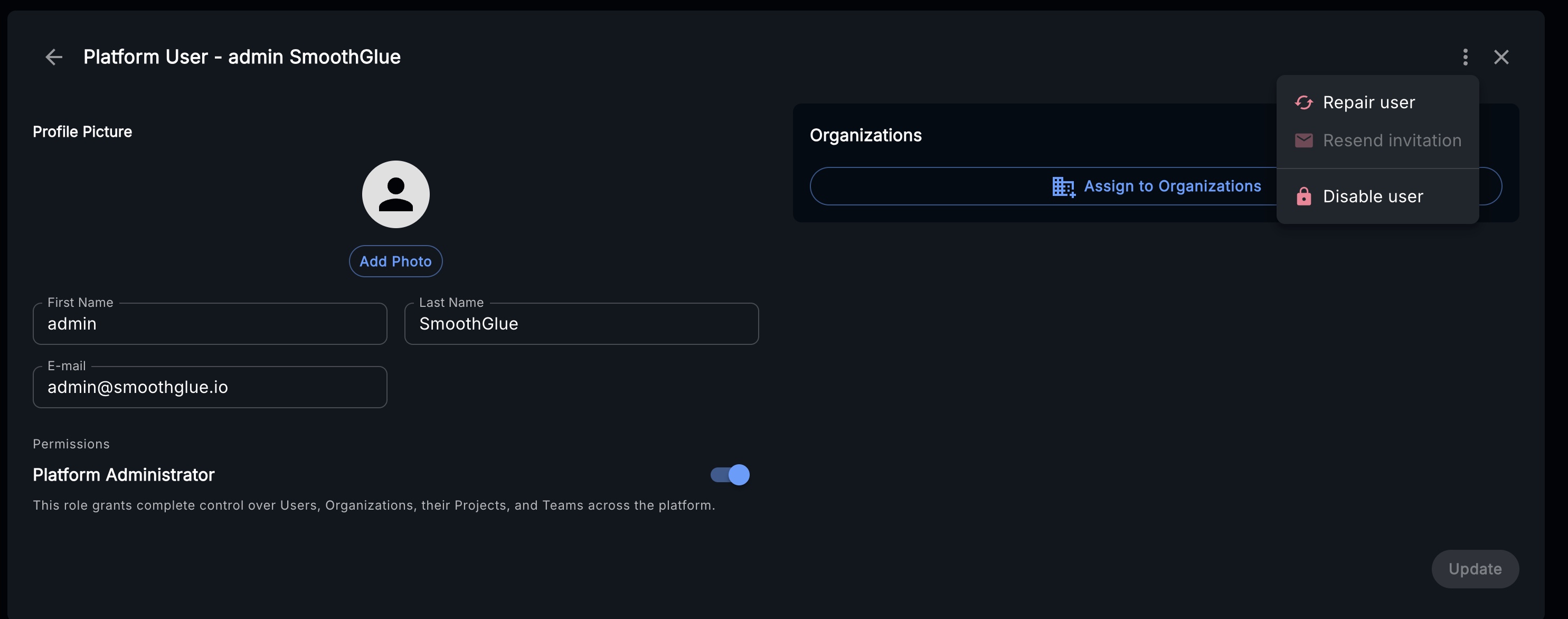
Upon successfully repairing, the user will fully setup.
To learn more about Console's capabilities, continue reading our Introduction to SmoothGlue Console.
More information on available configuration options and technical descriptions of Console actions can be found in the Console Technical Manual.